PPEE (Puppy) - Professional PE file Explorer for reversers and malware researchers

There are lots of tools out there for statically analyzing malicious binaries, but they are ordinary tools for ordinary files.
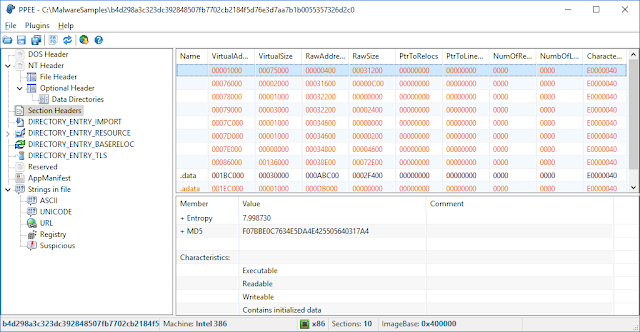
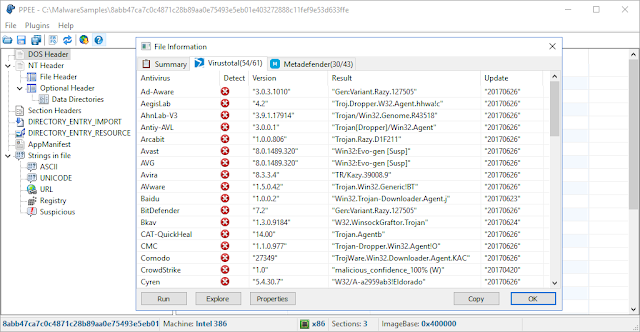
Puppy is a lightweight yet strong tool for static investigation of suspicious files. A companion plugin is also provided to query the file in the well-known malware repositories and take one-click technical information about the file such as its size, entropy, attributes, hashes, version info and so on.
Features
Puppy is robust against malformed and crafted PE files which makes it handy for reversers, malware researchers and those who want to inspect PE files in more details. All directories in a PE file including Export, Import, Resource, Exception, Certificate(Relies on Windows API), Base Relocation, Debug, TLS, Load Config, Bound Import, IAT, Delay Import, and CLR are supported.
- Both PE32 and PE64 support
- Examine YARA rules against opened file
- Virustotal and OPSWAT's Metadefender query report
- Statically analyze windows native and .Net executables
- Robust Parsing of exe, dll, sys, scr, drv, cpl, ocx and more
- Edit almost every data structure
- Easily dump sections, resources and .Net assembly directories
- Entropy and MD5 calculation of the sections and resource items
- View strings including URL, Registry, Suspicious, ... embedded in files
- Detect common resource types
- Extract artifacts remained in PE file
- Anomaly detection
- Right-click for Copy, Search in web, Whois and dump
- Built-in hex editor
- Explorer context menu integration
- Descriptive information for data members
- Refresh, Save and Save as menu commands
- Drag and drop support
- List view columns can sort data in an appropriate way
- Open file from command line
- Checksum validation
- Plugin enabled






Post a Comment